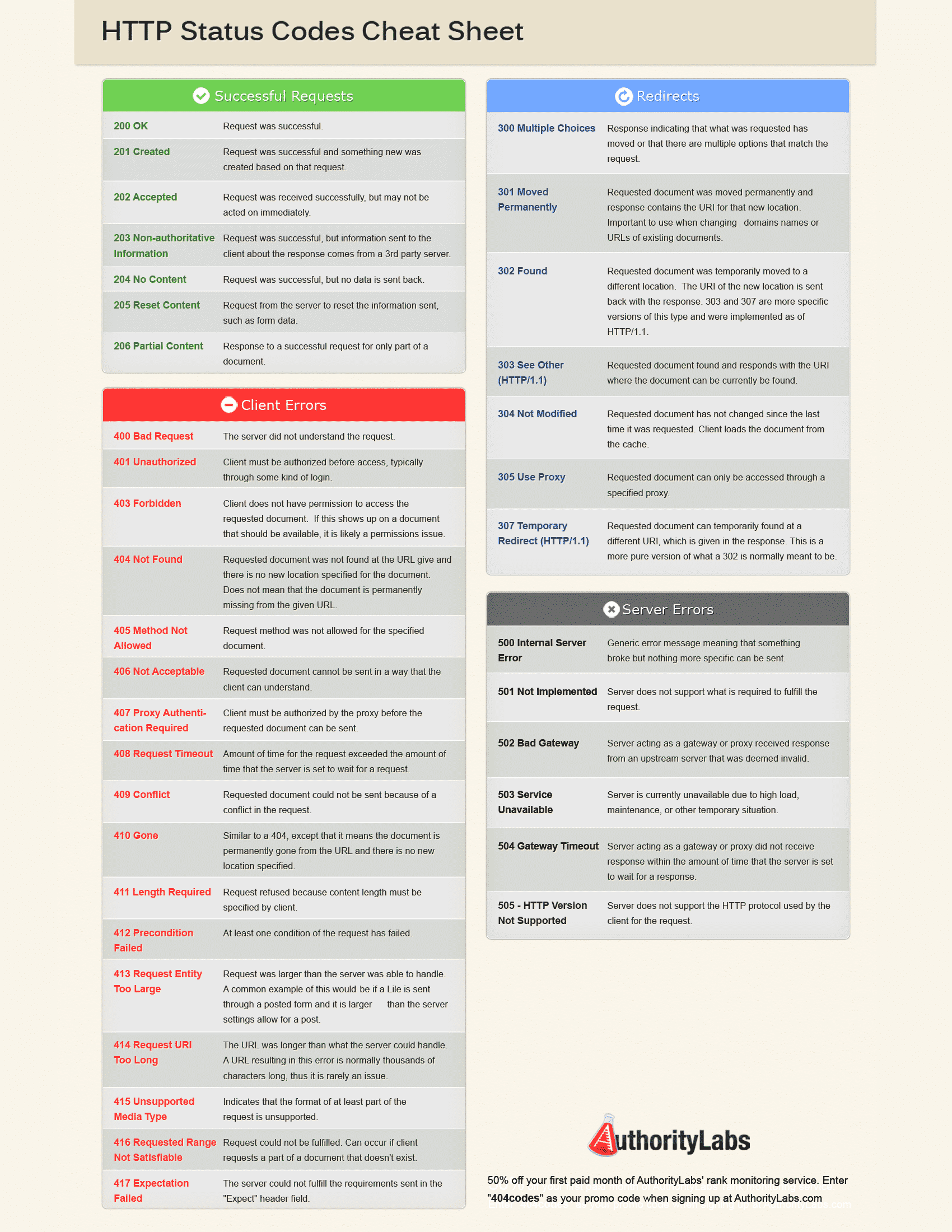
How To Cheat At Voip Security
Data: 1.09.2018 / Rating: 4.7 / Views: 918Gallery of Video:
Gallery of Images:
How To Cheat At Voip Security
Get the Basics of a VoIP Security Policy Use a sample VoIP Security Policy to understand the components of a complete policy. Provides system administrators with hundreds of tips, tricks, and. The Perfect Reference for the Multitasked SysAdmin This is the perfect guide if VoIP engineering is not your specialty. It is the perfect introduction to VoIP security, covering exploit tools and how they can be used against VoIP (Voice over IP) systems. The Perfect Reference for the Multitasked SysAdmin This is the perfect guide if VoIP engineering is not your specialty. It is the perfect introduction to VoIP security, covering exploit tools and how they can be used against VoIP (Voice over IP) systems. Buy the Paperback Book How To Cheat At Voip Security by Thomas Porter, Cissp, Ccnp, at Indigo. ca, Canada's largest bookstore. Get Free Shipping on Computers books over 25! The Perfect Reference for the Multitasked SysAdmin This is the perfect guide if VoIP engineering is not your specialty. Extra info for How To Cheat At VoIP Security. 9 The realtime nature of V o l P g e t there a second too late, and the packet is worthless. 9 Separation of data and signaling. Sessions, particularly unknown inbound sessions, that define addressing information for the data (media) channel in a discrete signaling channel do not. How to Cheat at VoIP Security by Thomas Porter, , available at Book Depository with free delivery worldwide. The Perfect Reference for the Multitasked SysAdmin This is the perfect guide if VoIP engineering is not your specialty. It is the perfect introduction to VoIP security, covering exploit tools and how they can be used against VoIP (Voice over IP) systems. It gives the basics of attack methodologies used against the SIP and H. 323 protocols as well as VoIP network infrastructure. Read Book Online Now to Cheat at VoIP Security This is the perfect guide if VoIP engineering is not your specialty. It is the perfect introduction to VoIP security, covering exploit tools and how they can be used against VoIP (Voice over IP) systems. It gives the basics of attack methodologies used against the SIP and H. If VoIP engineering is not your specialty, this guide provides an introduction to VoIP security, and covers exploit tools and how they can be used against VoIP systems. How to Cheat at Voip Security opis wydawcy: This is the perfect guide if VoIP engineering is not your specialty. It is the perfect introduction to VoIP security, covering exploit tools and how they can be used against VoIP (Voice over IP) systems. The Perfect Reference for the Multitasked SysAdminThis is the perfect guide if VoIP engineering is not your specialty. It is the perfect introduction to VoIP security, covering exploit tools and how they can be used against VoIP (Voice over IP) systems. Security on any VoIP network is of considerable importance, given the forensic importance of a phone call. On a conventional VoIP network, as well as on a traditional telephone network, the following information is logged. Buy How to Cheat at VoIP Security by Thomas Porter (ISBN: ) from Amazon's Book Store. Everyday low prices and free delivery on eligible orders. The Perfect Reference for the Multitasked SysAdmin This is the perfect guide if VoIP engineering is not your specialty. It is the perfect introduction to VoIP security, covering exploit tools and how they can be used against VoIP (Voice over IP) systems. Literatura obcojzyczna How to Cheat at Voip Security T. Porter w ksigarni internetowej BookMaster w cenie: 393, 30 z wysyka w 714 dni Zamw literatur obcojzyczn online. Zamawiajc telefonicznie: How to cheat at voip security literatura podaj numer katalogowy. how to cheat at voip security Download how to cheat at voip security or read online here in PDF or EPUB. Please click button to get how to cheat at voip security book now. All books are in clear copy here, and all files are secure so don't worry about it. how to cheat at voip security Download how to cheat at voip security or read online books in PDF, EPUB, Tuebl, and Mobi Format. Click Download or Read Online button to get how to cheat at voip security book now. This site is like a library, Use search box in the widget to get ebook that you want. Agar Security rakhen to media kehta hai bohat security hai, na rakhe to kehte hain security nahi rakhi: Ayaz Sadiq 03: 52 My Cheating Wife Cheated On MeNow What The Perfect Reference for the Multitasked SysAdmin This is the perfect guide if VoIP engineering is not your specialty. It is the perfect introduction to VoIP security, covering exploit tools and how they can be used against VoIP (Voice over IP) systems. The Perfect Reference for the Multitasked SysAdmin This is the perfect guide if VoIP engineering is not your specialty. It is the perfect introduction to VoIP security, covering exploit tools and how they can be used against VoIP (Voice over IP) systems. Email to friends Share on Facebook opens in a new window or tab Share on Twitter opens in a new window or tab Share on Pinterest opens in a new window or tab The Perfect Reference for the Multitasked SysAdmin This is the perfect guide if VoIP engineering is not your specialty. It is the perfect introduction to VoIP security, covering exploit tools and how they can be used against VoIP (Voice over IP) systems. Retrouvez How to Cheat at VoIP Security et des millions de livres en stock sur Amazon. Achetez neuf ou d'occasion Read How to Cheat at VoIP Security by Thomas Porter, CISSP, CCNP, CCDA, CCS with Rakuten Kobo. The Perfect Reference for the Multitasked SysAdmin This is the perfect guide if VoIP engineering is not your specialty. How to Cheat at VoIP Security (paperback). The Perfect Reference for the Multitasked SysAdmin This is the perfect guide if VoIP engineering is not your specialty. It is the perfect introduction to VoIP security, covering exploit tools and how they can be used against VoIP (Voice over IP) systems. The Perfect Reference for the Multitasked SysAdmin This is the perfect guide if VoIP engineering is not your specialty. It is the perfect introduction to VoIP security, covering exploit tools and how they can be used against VoIP (Voice over IP) systems. The Perfect Reference for the Multitasked SysAdmin This is the perfect guide if VoIP engineering is not your specialty. It is the perfect introduction to VoIP security, covering exploit tools and how they can be used against VoIP (Voice over IP) systems. The Perfect Reference for the Multitasked SysAdmin This is the perfect guide if VoIP engineering is not your specialty. It is the perfect introduction to VoIP security, covering exploit tools and how they can be used against VoIP (Voice over IP) systems. It gives the basics of attack methodologies. How to Cheat at Voip Security (How to Cheat) Michael Gough Thomas Porter. It is the perfect introduction to VoIP security, covering exploit tools and how they can be used against VoIP (Voice over IP) systems. It gives the basics of attack methodologies used against the SIP and H. 323 protocols as well as VoIP network infrastructure. The Perfect Reference for the Multitasked SysAdmin This is the perfect guide if VoIP engineering is not your specialty. It is the perfect introduction to VoIP security, covering exploit tools and how they can be used against VoIP (Voice over IP) systems. Thomas Porter Michael Gough Syngress Publishing, Inc. Learn more about How to Cheat at VoIP Security on GlobalSpec. [CISSP CCNP CCDA CCS Thomas Porter; Michael Gough The Perfect Reference for the Multitasked SysAdminThis is the perfect guide if VoIP engineering is not your specialty. It is the perfect introduction to VoIP security, covering exploit tools and. Book Description The Perfect Reference for the Multitasked SysAdmin This is the perfect guide if VoIP engineering is not your specialty. It is the perfect introduction to VoIP security, covering exploit tools and how they can be used against VoIP (Voice over IP) systems. By CCS Thomas Porter, Michael Gough. The ideal Reference for the Multitasked SysAdmin This is the best consultant if VoIP engineering isn't your uniqueness. it's the excellent advent to VoIP defense, protecting make the most instruments and the way they are often used opposed to VoIP (Voice over IP) structures. How to Cheat at VoIP Security by Thomas Porter, CISSP, CCNP, CCDA, CCS, Michael Gough The Perfect Reference for the Multitasked SysAdmin This is the perfect guide if. The Perfect Reference for the Multitasked SysAdmin This is the perfect guide if VoIP engineering is not your specialty. It is the perfect introduction to VoIP security, covering exploit tools and how they can be used against VoIP (Voice over IP) systems. The Perfect Reference for the Multitasked SysAdmin This is the perfect guide if VoIP engineering is not your specialty. It is the perfect introduction to VoIP security, covering exploit tools and how they can be used against VoIP (Voice over IP) systems. The Perfect Reference for the Multitasked SysAdmin This is the perfect guide if VoIP engineering is not your specialty. It is the perfect introduction to VoIP security, covering exploit tools and how they can be used against VoIP (Voice over IP) systems. It gives the basics of attack methodologies used against the SIP and H. 323 protocols as well as VoIP network infrastructure. for network security engineers and managers. One consequence of this convergence is that in the event of a major network attack, the organizations entire telecommunications infras tructure can be at risk. Securing the whole VoIP infrastructure requires planning, analysis. How to Cheat at VoIP Security Converging voice and data on the same wire, regardless of the protocols used, ups the ante for network security engineers and managers. One consequence of this convergence is that in the event of a major network attack, the organization's entire telecommunications infrastructure can. Opis i dane produktu How to Cheat at Voip Security. This is the perfect guide if VoIP engineering is not your specialty. It is the perfect introduction to VoIP security, covering exploit tools and how they can be used against VoIP (Voice over IP) systems. VoIP utilizes the same internet infrastructure, and it also uses the TCP, UDP, and other common protocols; it makes VoIP vulnerable to the common type of. The Perfect Reference for the Multitasked SysAdminThis is the perfect guide if VoIP engineering is not your specialty. It is the perfect introduction to VoIP security, covering exploit tools and how they can be used against VoIP (Voice over IP) systems. Download free ebook: How to Cheat at VoIP Security. By Thomas Porter, Michael GoughPublisher: Syngress 2007; 432 Pages; ISBN: ; File type: PDF. download
Related Images:
- The walking dead season 5 480
- Daw of the dead
- Mechanical fitter job interview questions answers
- La nuit nous appartient
- Extreme Survival Bunkers Special
- Arrested development s03 dvdrip
- Call of duty black ops black
- The return french
- Boardwalk empire s02e10 720p
- Lejos de Ella
- One piece 731
- Ghost in the shell
- ConvertXtoDVD 6 0 0 45 crack zip
- Great edm tracks
- These boots are made for walkin
- Real wife stories paige
- Activation key of windows 7
- La Imagen Fotografica En La Cultura Digital
- ECG Complete
- The mindy project s03e03
- Ball And Roller Bearings Theory Design And Application
- Cop land hindi
- Cbt nuggets
- Dr who theme
- Batman the movie lego
- Without words 1080p
- Murder in my house
- Va hard rock
- Einstein theory relativity
- Windows xp 2018 black
- Bet honors 2018
- Wall street ita dvdrip
- Colazione da tiffany ita
- Alvar Aalto in His Own Words
- You are not so smart
- Friends s07 bluray
- 2018 ita hits
- Faking it 1 temporada
- Mp3 hits 1988
- Biggles Pdf
- 64 bit windows 7 activator
- 03
- Toast 9 os x
- Mere yaar kaminey 720p
- Artemis fowl and the lost colony
- Download silver efex pro 2 full crack
- Vivegam
- Reality kings ariana marie
- Hercules greek audio
- The simpsons s19
- The game of thrones 2
- Marvels temporada 1
- JMP 13
- Kernel for NSF Local Security Removal
- Computer Fundamental Notes Pdf Download
- Rhythm sound
- Google translate 64 bit
- Age of ultron teaser
- Blu ray 720p
- Evil dead 2018 latino
- Gta sa crack download
- Bioinformatics with Python Cookbook
- My angel eyes
- Richie rich il pi ricco del mondo
- Grandfathergandhi
- Teen titans annual 02
- Reich clapping music score pdf
- Download game iggle pop full version gratis
- Active and Passive Thin Film Devices
- The tomorrow people s1e05
- C program dummie
- Feingold diet shopping
- Rimer London Rimer London
- Frozen dts 1080p
- 2004 the bourne supremacy
- Black sails 1x03
- Angularjs up and running